Most people have never heard of API, let alone understand what it does. Today, it is being used in various applications that we use daily. It is in use by big businesses such as Yelp to locate local eateries. People use APIs daily and are unaware of them.
Certain API security startups, are utilized when you wish to share a blog post, an article, or a recipe, and you click on the Facebook, Twitter, or LinkedIn little icon often at the top or on the sidebar, you are utilizing an API. Now that you have a basic understanding of how APIs are in use daily, let’s look at what an API is.
WHAT IS AN APPLICATION PROGRAMMING INTERFACE?
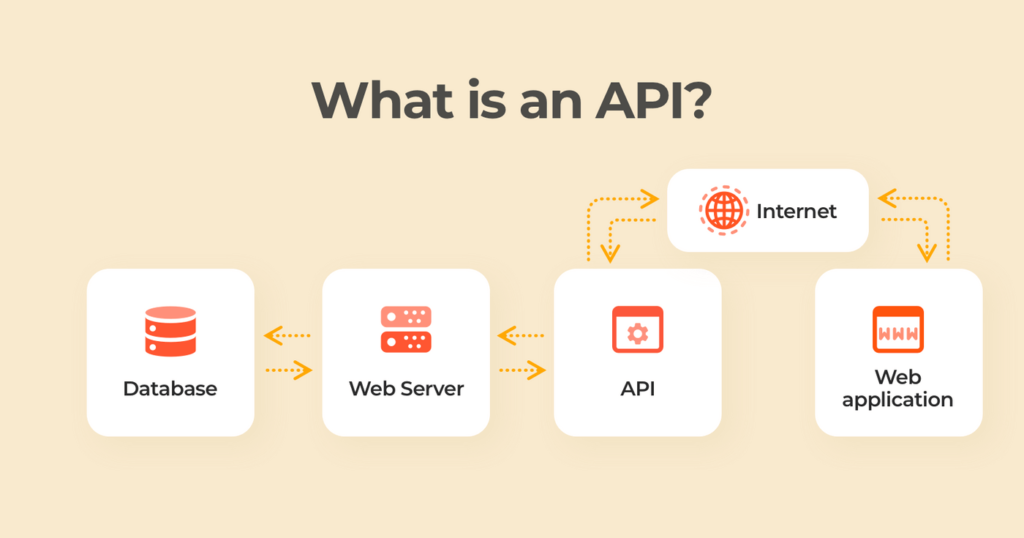
API stands for Application Programming Interface, which is a term that refers to the interfaces used by software to access data, server software, and other programs. APIs have existed for an extended period. In layman’s words, it is a software intermediate that enables communication between two apps. Consider an API to be a translator between two individuals who do not share a common language but can interact via a third party.
APIs are incredibly adaptable and used on various platforms, including web-based systems, operating systems, database systems, and computer components. Developers utilize APIs to increase their efficiency by reusing previously written code and modifying just the essential portions of the process. A good API simplifies developing a program by providing the necessary building elements. APIs use specified protocols to enable developers to construct, connect, and integrate applications rapidly.
WHAT IS AN API INTEGRATION?
“API integration” is a reasonably common Search engine term. APIs exist to facilitate integration. API integration is the process of utilizing APIs to link two (or more) applications, programs, processes, or systems. APIs enable applications to communicate by sending and receiving data and information.
HOW DO APPLICATION PROGRAMMING INTERFACES WORK?
APIs enable communication between programs, systems, and devices by sharing data and information.
Often, the simplest way to understand APIs is via the lens of a metaphor, and a popular one is that of a client, a waiter, and a restaurant kitchen: A client approaches the waiter and expresses his desires. The server records the order and passes it on to the kitchen. The kitchen prepares the dish, and then the waiter returns the customer’s order.
In this analogy, a client is analogous to a user, who communicates his desires to the waiter. The waiter functions similarly to an API, taking the customer’s request and converting it into simple-to-follow instructions that the kitchen uses to complete the order—often by following a particular set of codes, or input, that the kitchen readily recognizes.
Ideally, the kitchen functions similarly to a server, making the order according to the customer’s specifications! When the meal is ready, the waiter collects and delivers the order to the client.
WHAT PURPOSE DOES APIs SERVE?
• APIs are the foundation of desktop applications.
• APIs are the backbone of the majority of online applications.
• APIs enable the development of mobile applications.
• APIs are used to connect no-code solutions.
• APIs enable devices to communicate with the internet.
• APIs define networks—that is, the data exchanged between applications, systems, and devices.
• APIs are also used to link commonplace items such as autos, doorbells, dishwashers, and wearable gadgets.
API TYPES
While web APIs are often in use, there are others that you should have in mind. These are equally as dependable and effective as the web API but are less well-known.
REST (RESTful) API —
It signifies representational state transfer and uses the lightweight JSON language to communicate data. The majority of public APIs utilize this due to its high performance, reliability, and capacity to scale without harming the system as a whole. This API provides access to data through a standardized and specified set of operations. The HTTP protocol and URLs are what REST APIs
SOAP — Simple Object Access Protocol —
It is a bit more complicated than REST because it requires more preliminary information about sending messages. This API, which dates back to the late 1990s, transfers XML data, and it needs rigorous restrictions and enhanced security, which consumes additional bandwidth.
This protocol is not cacheable, has rigorous communication requirements, and requires every bit of information about an encounter before any calls are to be considered for processing.
XML-RPC — often called extensible markup language —
It is an acronym for Remote Procedure Calls. This protocol, which is older and easier than SOAP, transfers data using a particular XML format. A client initiates an RPC by submitting an HTTP request to an XML-RPC-compliant server and receiving the HTTP response.
JSON-RPC —
It is highly similar to XML-RPC in that they both operate in the same manner, except that this protocol uses the JSON format rather than the XML format. Usually, the client is the software that invokes a single approach on the remote system.
10 TOP API SECURITY STARTUPS
1. Noname Security
Noname Security is a comprehensive API security solution that protects your APIs against data leakage, permission difficulties, abuse, misuse, and data corruption without the usage of agents or network changes. Additionally, it analyzes APIs and user activity to identify and prevent weaknesses and breaches.
Noname spends time understanding your API inventory and gaining comprehensive insights into your APIs, users, data, and third-party interactions, all without using agents or modifying your network. Integrate your on-premises and cloud environments, SIEM software, API gateway, and project management tools completely.
2. Ubiq Security
Ubiq’s goal is to enable developers to integrate encryption straight into their apps without prior knowledge or skill in encryption. Ubiq’s mission is to simplify and standardize encryption for software developers and data security teams.
That is, lowering obstacles to encryption enables wider adoption, saves developers time, and removes downstream security expenses, allowing enterprises to mitigate risk and devote their time and resources to building their business.
3. Solo.io
They contribute to transforming application architectures to cloud-native architectures by linking application services, service meshes, clusters, and clouds. Solo provides two products: Gloo Edge, an API gateway for application traffic, and Gloo Mesh, a control plane for service meshes.
Solo‘s unified control is dependable and should build the security on industry-leading open-source Istio and Envoy Proxy. Additionally, they minimize your work and risk, allowing you to focus on creativity in your applications.
4. Blackbird.AI
Blackbird’s mission is to improve decision-making and empower those committed to information integrity. They feel that misinformation is one of the most severe global concerns of our day, posing a threat to national security, enterprise business, and the general people.
They intend to bring to light those who strive to distort and divide. Blackbird. AI provides national security and corporate customers with disinformation defense and response capabilities. The AI Platform enables businesses to guard against and respond to new cyberattacks on human understanding and the manipulation processes that underpin them.
5. Hazy
Hazy creates statistically controlled simulated data to correct class imbalances, accelerate data innovation, and assist in forecasting the future. Class unbalanced data sets are a significant source of frustration in financial data science, particularly in areas such as fraud modeling, credit risk analysis, and low-frequency trading.
Hazy Balance revamps structured data sets appropriately by utilizing various best-in-class methodologies, enhancing low-frequency signals, allowing models to be trained on more data, resulting in improved outcomes.
6. Corsha, Inc.
They contribute to API security simplification and enable companies, developers, and DevSecOps teams to embrace modernization, complicated deployments, and hybrid environments confidently. Corsha is a well-funded cybersecurity business based in the Washington, D.C. metro region with revolutionary API security solutions.
The fundamental technology is dual-purpose, straightforward to install and deploy for commercial and government customers. Corsha’s technical staff is robust, with extensive experience in distributed ledgers, cryptography, security concepts, orchestration technologies, and software design.
7. Abnormal Security
Abnormal security’s cloud-based email security software safeguards businesses against targeted email threats. The platform, driven by Abnormal Behavior Technology (ABX), blends the Abnormal Identity Model, the Abnormal Relationship Graph, and Abnormal Content Analysis to help avoid account takeovers, financial loss, and corporate distrust.
Abnormal security installs in minutes, involves no configuration, and affects email flow due to its one-click, API-based Office 365 and G Suite connection.
8. API3
The decentralized API infrastructure provided by API3 connects blockchain applications to off-chain data providers, facilitating next-generation use situations in financial derivatives, synthetic assets, prediction markets, and insurance products while maintaining the highest security standards.
9. Traceable
Given the rapid development speed and new threats to apps, Traceable helps Security control application and API risks. Traceable secures contemporary applications and APIs by combining the power of end-to-end distributed tracing, cloud-native connectors, and powerful behavioral analytics.
Specifically designed for cloud-native applications, Traceable secures transactions natively in Kubernetes, Envoy Service Mesh, Serverless, and other cloud-native environments.
10. Modex
They assist organizations, enterprises, and individuals in safeguarding their digital data. The system ensures the integrity and security of data in real-time, as well as permission-based access and data exchange protocols.
They assist firms in gaining a competitive edge on the market by using their extensive expertise in offering corporate blockchain services, tools, and frameworks that suit a range of industry-specific demands.
Modex BCDB is a middleware that combines a blockchain with a database to produce an intuitive framework that developers with no prior understanding of blockchain development may use and comprehend. Consequently, any developer familiar with database systems may use our solution without changing their programming style or learning blockchain.
FAQ
What is the most secure API?
Each web API should utilize TLS (Transport Layer Security). TLS encrypts your API’s communications in transit (as well as the messages your users submit to your API).
How can I validate the Security of an API?
The API must return the expected value for a given input. For the most part, inputs must fall within a specified range and reject values outside the field, and incorrectly typed inputs dismissed.
What is an application programming interface in the context of information security?
API security is an umbrella word that refers to procedures and technologies that protect application program interfaces from malicious attacks or misuse (API). APIs are becoming a target for hackers as they have grown critical to developing web-based interactions.
Is it possible to hack an API?
Some APIs are accessible over the internet, while others are exclusively accessible internally. One of the most straightforward API hacking techniques is to exploit APIs that should be off-limits to hackers.
What exactly is an OAuth server?
OAuth is an open-standard authorization protocol or structure that explains how unconnected servers and services can provide authenticated access to their resources without sharing the original, associated, single login credential.
CONCLUSION
APIs are a powerful tool that may assist you in various ways, including speeding up your company processes, expanding your brand’s reach, connecting your customers to the items they desire, and much more. If you’re interested in learning more about how API may help you power your business, the best API security startups listed above might serve as a guide.
REFERENCES
Our Writers most times refer to other reputable publishers source to bring in more facts especially when it has to do with stats
PostMan: You could read more on API here
Cover Image: Techcrunch